You might want to read my prior articles on Android/BianLian first: unpacking, payload, fake server.
There was a remaining point which was bugging me: how does the Android/BianLian bot know where to contact the C&C?
Having worked on the samples for several days, I noticed they weren’t always heading to the same website: hxxp://rheacollier31532[.]website, hxxp://shanehook85484[.]website etc.
So, where do those names come from? Is this from a Domain Generation Algorithm (DGA)? or are they hidden in an asset?
Answer: the active C&C is returned by a malicious GitHub user account. The account name unfortunately varies from one sample to another:
hxxps://gist.githubusercontent.com/ferrari458italy/4fe02ee186816abcfcca6eaaed44659d/raw/helloworld.jsonhxxps://gist.githubusercontent.com/monopolyofficial/e0656a5a4d04af06e2af9ed83aa0c868/raw/helloworld.json- …
The json page actually contains a Base64-encoded JSON object with the C&C’s URL:
$ curl https://gist.githubusercontent.com/monopolyofficial/e0656a5a4d04af06e2af9ed83aa0c868/raw/helloworld.jsoneyJkb21haW5zIjpbImh0dHA6Ly9mdWxsdmVoZHZpZGVvaXpsZW1lYXlhcmxhcmk0NTQ1LnNpdGUi
XX0K
$ echo "eyJkb21haW5zIjpbImh0dHA6Ly9mdWxsdmVoZHZpZGVvaXpsZW1lYXlhcmxhcmk0NTQ1LnNpdGUiXX0K" | base64 -d
{"domains":["http://fullvehdvideoizlemeayarlari4545.site"]}How does the code work?
- At first, the code sets a Property with a decrypted admin URL.

2. Actually, as the shared preferences file has no C&C yet, this will actually return a dummy C&C https://www.google.com

3. The real C&C is retrieved from the init procedure
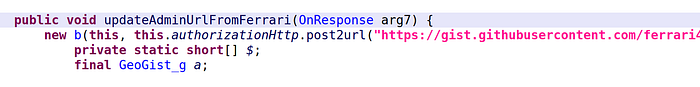
com.pmmynubv.nommztx.bot.g.b4. The code retrieves the “domains” parameter of the JSON
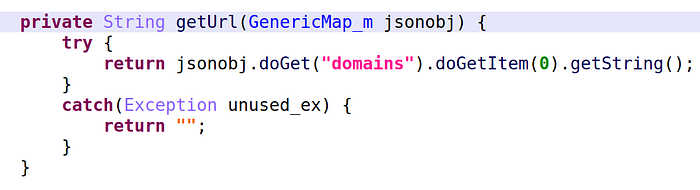
5. Finally, the code sets the URL in the shared preferences.

com.pmmynubv.nommztx.bot.g.aConclusion: there is no DGA algorithm. It is just a hard-coded remote URL serving an updated C&C name.
— the Crypto Girl
